New Data on Security Habits Pinpoints the Riskiest Business Users
While 93% of office workers admit to insecure IT practices, Intermedia’s 2015 Insider Risk Report finds that tech-savvy users are actually the worst offenders
Tech-savvy employees actually create the MOST security risks? #RiskiestUsers Data via @intermedia_net Tweet
PR Newswire – Mountain View, CA – October 21, 2015
Intermedia today released its 2015 Insider Risk Report, which exposes the online security habits of more than 2,000 office workers in the U.S. and U.K.
Even as businesses and the federal government have made cybersecurity a high priority, Intermedia’s survey found that 93% of office workers engage in some form of unsafe online habits that could jeopardize their employer or their customers.
GALLERY
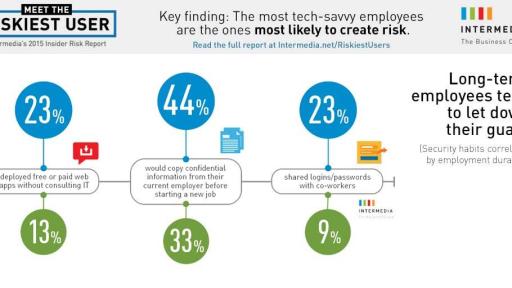
The most tech-savvy employees are most likely to create risk
More surprising, the very people who have the greatest access to company data and are tasked with keeping the company secure—IT personnel—are much more likely to engage in risky behaviors than the average employee:
Download the full text of
Intermedia’s 2015 Insider Risk Report
- 32% of IT professionals have given out their login / password credentials to other employees (compared to 19% across all respondents)
- 28% of IT pros said they have accessed systems belonging to previous employers after they left the job (compared to only 13% among all respondents)
- 31% of IT pros said they would take data from their company if it would positively benefit them – nearly three times the rate of general business professionals
These kinds of practices create risks that include lost data, regulatory compliance failures, data breaches, eDiscovery complications, ex-employee access, and even out-and-out sabotage by a disgruntled current or former employee.
Scope of report findings beyond IT pros
Intermedia’s report also includes data across a range of industries, such as healthcare, finance and legal services, as well as across job functions. Additionally, it examines security habits across age group, company size and job tenure.
Within these categories, a few of the additional insights highlighted within the full report include:
- Millennials are most likely to breach the personal and professional computing divide by installing apps without company approval, saving company files to personal cloud storage, or engaging in other risky “Shadow IT” practices
- By employment duration, long-term employees (7+ years) tend to introduce greater overall security risks
Intermedia’s report offers businesses a better understanding of the scope of the insider threat problem. 97% of respondents have access to sensitive or confidential company information, which means it’s imperative for companies to offer IT tools that make it simple for users to adhere to company security policies.
Resources
- Online highlights from Intermedia’s 2015 Insider Risk Report
- 68 second video: “Meet Jeff. The business world’s riskiest user.”
- Intermedia’s 2015 Insider Risk Report (full PDF)
- Best practices for preventing insider risk (PDF guide)
- What kind of risks do ex-employees create? Read Intermedia’s 2014 Rogue Access Report
Quotes
“I’m particularly worried about ex-employee access. What kind of access do employees walk away with when they leave? If they go to a competitor, what kind of damage can they do? People usually delete stuff when they leave, which is bad enough—but it’s really bad when they can come back a few months later and wreak havoc. Especially if it’s IT people with that access. That bothers me the most.”
- Felix Yanko, President, ServNet
“It’s nearly always that technical people are the worst offenders. They know how to get around various controls that an IT team will put in place. It’s sometimes done with the best intent, but nevertheless with a complete lack of consideration for the risk or security implications.”
- Richard Walters, VP of Identity & Access Management, Intermedia
“Security policies are most effective when employees don’t even have to think about them. That’s why it’s so important to provide tools that make it easier to follow the rules, like single sign-on portals or enterprise-class file sharing. The simpler it is for employees to be productive using company sanctioned tools, the more likely you are to deter the kinds of practices that put the company at risk.”
- Jonathan Levine, CTO, Intermedia
Survey methodology
This study was commissioned by Intermedia and delivered by Precision Sample®, an independent market research organization. Precision Sample has an active proprietary panel of over 3.5M respondents that is routinely validated with a stringent screening process including Verity® and RelevantID by Imperium®. Results derived from a 10-minute online survey instrument with 34 total questions, fielded August 4-6, 2015. Setup questions were used to ensure that only office workers were in the sample, which was defined as those who use a computer, laptop, smartphone or tablet in their day-to-day work. Overall margin of error of +/- 2.17% at a 95% confidence interval.
About Intermedia
Intermedia is a one-stop shop for cloud business applications. Its Office in the Cloud™ integrates email, voice, file sync and share, security and many other essential IT services—and supports customers and partners with a Worry-free Experience™. For more information, visit Intermedia.net.
Dan Walsh
LEWIS PR
415.432.2400
[email protected]